- Home
- About Us
-
- Frequently Asked Questions about ContentProtector.eu
- Certification Demo
- How to present the Certification as Legal Evidence
- Timestamp Verification
- Preventive Protection of Strategic Business Content
- ContentProtector vs Traditional Digital Signature
- ContentProtector vs Blockchain: which Certification to Choose for Legal Evidence
- Contacts
- Home
- About Us
-
- Frequently Asked Questions about ContentProtector.eu
- Certification Demo
- How to present the Certification as Legal Evidence
- Timestamp Verification
- Preventive Protection of Strategic Business Content
- ContentProtector vs Traditional Digital Signature
- ContentProtector vs Blockchain: which Certification to Choose for Legal Evidence
- Contacts
Frequently Asked Questions (FAQ)
All the Answers about ContentProtector.eu
Do you have questions about ContentProtector.eu? Here you will find all the answers
We have collected the most frequently asked questions to help you understand how our digital certification system works. In just a few seconds you can legally protect any content, track access, obtain reliable proof, and safeguard yourself in case of disputes.
❓ What is ContentProtector.eu?
ContentProtector.eu is an advanced forensic certification system for your digital files.
With just one click you get upload date, unique hash, tracking data (including the recipient’s IP), and a technical page ready for certification. Optionally, you can activate the qualified RFC 3161/eIDAS timestamp to obtain immediate legal value throughout the European Union.
With a qualified timestamp: the certification already has full immediate legal value in compliance with the eIDAS Regulation (EU 910/2014). Without a timestamp: to obtain full evidential value in case of a complaint or litigation, you can request the authentic forensic copy of your certification: a fast and secure procedure, because the system has already prepared all the necessary evidence.
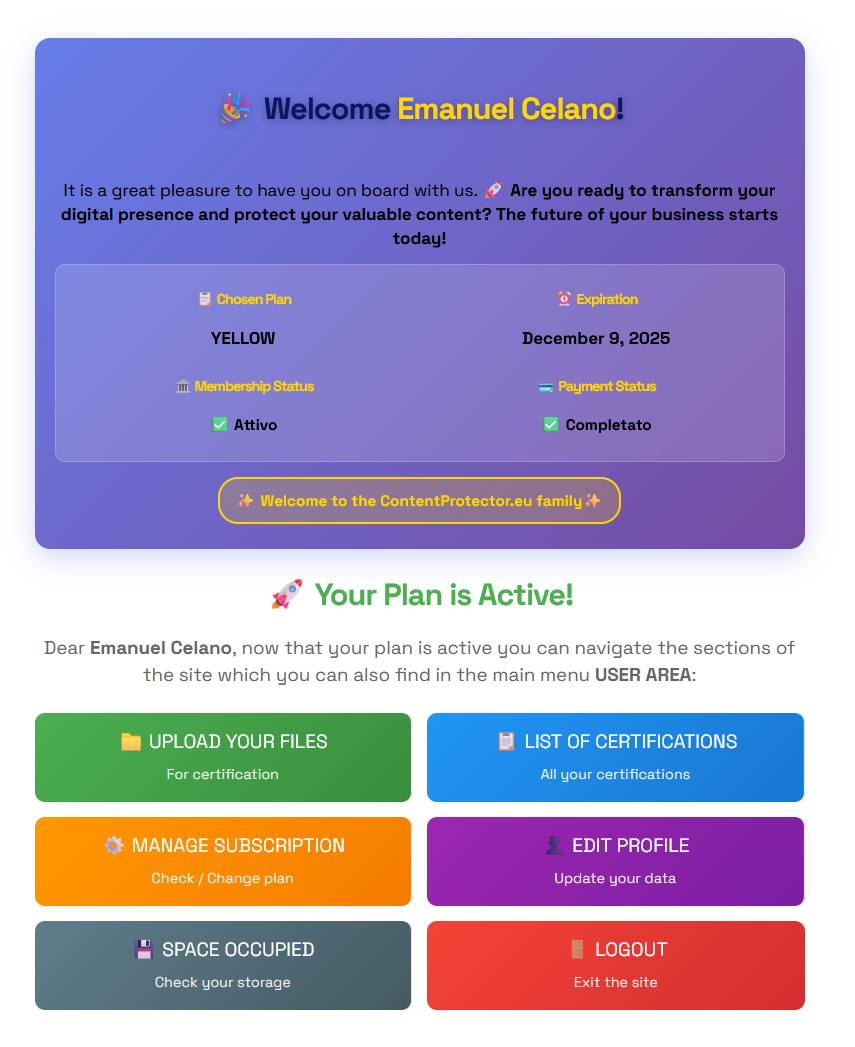
Below, an example of the Dashboard reserved for registered users:
❓Why am I asked to provide the number of an identity document?
Why am I asked to provide the number of an identity document?
We request only the document number (not a photo or a copy of the document) for security reasons related to protecting your account and the digital content you certify with ContentProtector.eu. Specifically, this information helps us in two critical scenarios:
-
Secure account recovery:
in exceptional cases (for example, if you permanently lose access to your email), the document number allows us to verify that the recovery request truly comes from the legitimate account owner before reactivating or modifying access to sensitive certified materials (such as industrial secrets, confidential files, personal or intimate images, etc.). -
Protection in case of account theft or false ownership claims:
if someone attempts to regain access by falsely claiming to be the owner, we can verify the information provided against the data recorded during registration. This offers an additional layer of protection against fraudulent access attempts and safeguards your certified content.
The document number is used exclusively for these security checks and to ensure the legal validity of the service. It is never shared with third parties and is stored in a protected form, fully compliant with GDPR and the highest security standards.
❓Service usage images and certification page
If you would like to see how the service works through sample images, please visit this page: Present the certification as legal evidence and select the tab named “Service usage images and certification page”
❓ What is the purpose of certifying a file?
Certifying a file with ContentProtector.eu allows you to prove precisely when it was uploaded to the platform, what it contains, and to whom it was sent.
All this information is securely recorded and stored, with a digital fingerprint (hash) and, if enabled, recipient tracking with IP and technical details. With a qualified RFC 3161/eIDAS timestamp, you also obtain certified legal date and time in compliance with EU Regulation 910/2014.
This documentation becomes particularly useful in cases of:
- disputes over who created a piece of content or when it was sent;
- legal actions for intellectual property theft or contractual violations;
- online fraud;
- unauthorized distribution or misuse of sensitive files.
The certification allows you to have concrete, technical, and impartial evidence, ready to be used even in court. With a qualified timestamp, evidential value is immediate across the EU; without a timestamp, you can later request the forensic authentic copy for full legal value.
❓ I already have a digital signature, isn’t it the same thing?
The differences are substantial across 8 fundamental points that make ContentProtector.eu superior:
🎯 Proof of Prior Existence
Digital signature + timestamp: Certifies only the moment of signing, not the prior existence of the file. You can prove that on January 10th you signed that document and that it wasn’t modified afterward, but you cannot prove: that the file existed before that date, that it wasn’t altered shortly before signing, that a previous version was identical. Result: no enforceable proof of prior existence.
ContentProtector.eu: You can prove that on January 10th that file already existed in that exact form (certified SHA-256 hash). By comparing hashes today, you prove it’s identical. Prior existence becomes enforceable: you demonstrate when the file existed and that it was exactly identical to the current version. Integrity certified before signing. Result: verifiable and legally enforceable proof of prior existence.
🔓 Immediate Content Accessibility
Digital signature + timestamp: The signed file (.p7m, .tsd, signed .pdf) is not immediately accessible. Recipients must download dedicated software (Dike, ArubaSign, etc.), install verification certificates, and understand complex technical procedures. Result: access barrier that limits sharing.
ContentProtector.eu: The original file always remains intact and openable by anyone: videos open with any player, audio playable anywhere, images viewable in any browser, documents readable without additional software. Result: maximum accessibility + legal protection.
📊 Impossible vs. Complete Tracking and Monitoring
Digital signature: Once the signed file is sent, it’s impossible to know who opened it and when, from which device or IP, if it was shared with third parties, where the user is geographically located. Provides no evidence of recipient behavior. Zero post-delivery control.
ContentProtector.eu: Complete tracking with legal value: precise geolocation 🌍, device and browser type 📱, date and time of each access ⏰, real-time email notifications 📧, social media access blocking 🚫. This data is very useful in legal proceedings. Total control + enforceable digital evidence.
☁️ Storage and Management
Digital signature: Includes no storage system: you must manage archiving yourself, risk losing signed files, no centralized dashboard, complex sharing. Manual and fragmented management.
ContentProtector.eu: Complete integrated ecosystem: secure cloud storage included 🏛️, dashboard to manage all certifications 📋, protected links for immediate sharing 🔗, detailed usage statistics 📊, permanent accessibility from your personal area. Everything in one professional platform.
🔮 Long-term Proof Duration
Digital signature: Risk of technological obsolescence: in 10 years the software might no longer exist, proprietary formats (.p7m, .tsd) might not be supported, verification certificates might expire, dependence on software that changes over time. Potentially unusable proof in the future.
ContentProtector.eu: Guaranteed eternal proof: SHA-256 hash is an immutable universal standard, .TSR file readable with always-available public tools, RFC 3161 standard is a permanent global protocol, independent verification possible at pkitools.net ↗. Verifiable forever, without proprietary dependencies.
✍️ Certifying Authority
Personal digital signature: The signature is tied to an individual: can be contested or disowned, depends on personal certificate validity, requires SPID/CNS identification, individual responsibility, focus on “who” signs. Subjective and potentially contestable certification.
ContentProtector.eu: Certification by European Qualified Entity: eIDAS-compliant qualified TSA 🇪🇺, ETSI EN 319 421/422 standards 📜, automatic EU legal recognition ⚖️, independent third-party authority 🏛️, focus on “what” you protect, not who you are. Superior probative value and objective certification.
🛡️ Preventive Legal Deterrence
Digital signature: It’s just a silent technical act: recipients receive no warnings, no copyright communication, zero preventive deterrence, no legal guidance for the sender. No dissuasive effect.
ContentProtector.eu: Integrated legal protection system: automatic legal texts in multiple languages 📜, clear copyright warnings ⚠️, communication of legal consequences 🚨, effective psychological deterrence 🛡️, integrated warnings visible to recipient. Active violation prevention with immediate deterrent effect.
⚡ Simplicity and Operational Speed
Digital signature + timestamp: Long and complex process: minimum 15-20 minutes required ⏱️, physical token or dedicated software needed 🔑, multiple PIN and password entries 🔢, technical skills required 💻, cost for each timestamp 💰, procedure that discourages frequent use. Complexity that limits adoption.
ContentProtector.eu: Immediate and intuitive: 1 click = complete certification ⚡, drag & drop upload 📤, process completed in 30 seconds 🏃♂️, usable by anyone without technical skills 👶, everything included in plan: hash + timestamp + storage + tracking 💎, no hardware or token required. Extreme simplicity for daily use.
📊 Complete Technical Comparison Table
| Topic | Digital Signature + Timestamp | ContentProtector |
|---|---|---|
| Proof of prior existence | ❌ No | ✅ Yes |
| Certain date | ✅ Yes | ✅ Yes |
| Integrity after signing | ✅ Yes | ✅ Yes |
| Integrity before signing | ❌ No | ✅ Yes |
| Original file accessibility | ❌ No (requires software) | ✅ Yes (any device) |
| Access tracking | ❌ No | ✅ Yes (IP, GEO, time) |
| Storage system | ❌ No | ✅ Cloud + Dashboard |
| Universal verifiability | ❌ No (specific software) | ✅ Yes (public hash) |
| Certifying authority | ⚠️ Individual person | ✅ eIDAS Qualified Entity |
| Obsolescence risk | ⚠️ High (proprietary formats) | ✅ Low (universal SHA-256) |
| Preventive deterrence | ❌ No | ✅ Integrated legal notices |
| Time required | ⏱️ 15-20 minutes | ⚡ 30 seconds |
💡 Practical Example: Real Scenario
Situation: On January 10th you created the file Preliminary_Contract.pdf.
You certify it in two ways:
- A) Digital signature + timestamp
- B) ContentProtector (hash + TSA + JSON + tracking)
On June 18th the counterparty contests that the document was created “ad hoc” after an event that occurred on May 15th. You must prove prior existence.
❌ With Digital Signature + Timestamp:
- ✓ You prove you signed the file on January 10th
- ✓ You prove the file wasn’t modified after signing
- ✗ You CANNOT prove the file existed before that date
- ✗ You CANNOT prove it wasn’t modified shortly before signing
- ✗ You CANNOT prove a previous draft was identical
Result: The counterparty can claim you created the document after May 15th and signed it on January 10th with a backdated timestamp.
✅ With ContentProtector:
- ✓ You prove the file had exactly that SHA-256 hash on January 10th
- ✓ The hash is certified by eIDAS-qualified TSA
- ✓ By comparing the current file’s hash with the certified one, you prove it’s identical
- ✓ Prior existence is enforceable: the file existed in that form before May 15th
- ✓ The certification is independently verifiable by anyone
- ✓ Any access is tracked with IP, time, and device
Result: You have incontestable proof that the document existed in that exact form on January 10th, therefore before May 15th.
🎯 In Summary
Traditional digital signature is a technical tool of the past 📜
ContentProtector.eu is an integrated legal ecosystem of the future 🚀
The two solutions are not mutually exclusive:
– Digital signature protects who signs
– ContentProtector protects what was created
Used together, they offer the strongest evidentiary chain available.
❓ Which professionals can benefit from the service?
Discover the full list of professions and sectors that can benefit from the legal certification of digital content, with practical examples of use.
👉 Check the complete list on this page
❓ What can I certify?
You can certify any type of digital file, with no limits of format or category.
Among the most frequently protected contents are: images, videos, documents (PDF, Word, Excel), audio files, compressed archives (ZIP, RAR) and confidential projects such as source code, graphic layouts, draft contracts or creative content intended for clients or online platforms.
Each uploaded file receives:
- a SHA-256 hash, which is a unique digital fingerprint ensuring content integrity;
- a technical certification page, with precise upload date and time;
- and, if you wish to send it, a tracking link that also records the recipient’s access data (IP, device, time);
- optionally, qualified timestamp RFC 3161/eIDAS which grants the certification immediate legal value in compliance with EU Regulation 910/2014.
Thanks to this evidence, you can prove the existence and transmission of the file with forensic accuracy. With a qualified timestamp you obtain immediate probative value throughout the EU; without a timestamp you can later request the forensic authentic copy for full legal value.
❓ Privacy, GDPR and Regulatory Compliance
🔒 Privacy, GDPR and Regulatory Compliance
A comprehensive response to privacy, data protection and compliance with the European GDPR Regulation for ContentProtector.it can be found here: https://contentprotector.eu/privacy-policy/
❓ Is my file also legally protected?
Yes, the ContentProtector.eu system is designed to generate structured digital evidence that immediately acquires forensic value with a qualified RFC 3161/eIDAS timestamp, or through an optional authentic copy that the user can request later if needed. Each uploaded file is associated with a certifiable technical page, containing key elements such as a unique hash, upload date, and, if enabled, recipient access tracking.
With a qualified timestamp: the evidence has immediate legal value in compliance with EU eIDAS Regulation 910/2014, and can be used directly in legal proceedings. Without a timestamp: to make the evidence legally enforceable, for example in a complaint, contractual dispute, or online platform report, you can request the forensic authentic copy of the certification: a signed, exportable, and verifiable document that records all data collected at the time of the file upload on the site.
Thanks to this system, you can safely act in:
- civil or criminal cases;
- content removal procedures;
- contractual or compensation disputes;
- protection of intellectual or personal property online.
All this happens without the need for complex tools or technical expertise, because the evidence is already prepared and stored with forensic criteria. With a qualified timestamp, probative value is guaranteed immediately throughout the European Union.
❓ Can I certify that the file has been opened?
Yes, thanks to the tracking link from ContentProtector.eu you receive an instant notification as soon as the recipient opens the file you sent. This feature is invaluable for documenting the actual opening and receipt of the content, and is accompanied by a detailed technical record. With a qualified RFC 3161/eIDAS timestamp, all this data acquires immediate legal value.
The data collected includes:
- Exact date and time of the file opening
- Public IP address of the recipient
- User Agent (operating system, browser type and version)
- Referer (if available)
- UID or user code
- Certification Number
All this data is permanently stored, digitally signed, and included in the file’s certifiable technical page. With a qualified timestamp it has immediate evidential value in compliance with EU eIDAS; without a timestamp you can later request an authentic copy of this page to obtain evidential value in any legal or dispute situation.
Finally, a SHA256 hash of the link itself is generated for:- 🔐 Email Authenticity: Ensures the notification really comes from our system and has not been falsified
- 🧾 Unique Proof: Creates a unique cryptographic fingerprint of that specific link at that precise moment
- ⚖️ Evidential Value: Provides an additional technical element usable as evidence in potential legal disputes (immediate with qualified timestamp)
- 🛡️ Anti-Forgery: Makes it impossible to create fake emails that appear to come from our service
- 🔍 Retroactive Verification: Allows verification in the future that the email referred exactly to that specific link
❓ Can I send confidential content and track it?
Yes, you can send a secure and tracked link to the recipient, automatically generated by the system at the time of file upload. This link allows not only content sharing, but also access monitoring, providing a concrete guarantee of delivery. With a qualified RFC 3161/eIDAS timestamp, your file acquires immediate legal value.
Thanks to advanced tracking, no one will ever again be able to claim:
“I didn’t receive it”, “I never opened it” or “that wasn’t the file”.
Each file opening, up to a maximum of 5 times, is recorded and communicated via email:
- Exact date and time
- Recipient’s IP
- Device and browser used
- SHA-256 hash of the link to guarantee notification authenticity
This is your definitive digital proof that the file was actually received and viewed by the correct recipient. With a qualified timestamp you obtain immediate evidential value compliant with EU Regulation eIDAS 910/2014; without a timestamp you can later request the forensic authentic copy for full legal value.
❓ How can I prove that the file is mine / created by me first?
🏆 RECOMMENDED SOLUTION: QUALIFIED RFC 3161/eIDAS TIMESTAMP
With the qualified timestamp option, you immediately obtain:- 🏛️ Immediate legal certainty compliant with EU eIDAS Regulation 910/2014
- ⚖️ Qualified evidential value under art. 2702 of the Civil Code, equivalent to a private deed
- 🔒 Opposability erga omnes – contestable only by filing a false-claim procedure
- 🇪🇺 Recognition throughout the European Union without further checks
- 🎯 Complete proof: SHA-256 hash + legally certified date in one single solution
📧 ALTERNATIVE: AUTOMATIC EMAIL (without timestamp)
Without a qualified timestamp, you will still receive an automatic email that falls under digital reproductions pursuant to art. 2712 of the Civil Code and can serve as documentary evidence of the upload, supported by the technical metadata contained in the headers (server timestamp, routing path, SPF, DKIM, DMARC). The combination of:- Unique file SHA-256 hash
- Automatic server timestamp
- Email headers verifiable with SPF, DKIM and DMARC checks
- Certified automated system
- 🔐 Unique fingerprint: only that specific file can generate exactly that hash
- ⚖️ Qualified technical proof: extremely difficult to challenge authenticity
- 🛡️ Integrity guarantee: any modification would completely change the hash
- 🎯 Burden of proof reversal: the opposing party must prove that the hash is false
🏛️ FORENSIC AUTHENTIC COPY (additional service)
If you chose the automatic email option, you can later request the forensic authentic copy, produced with qualified software and digitally signed with a timestamp, obtaining:- Qualified evidential value under art. 2702 of the Civil Code
- Legal presumption of conformity contestable only through a false-claim procedure
- International forensic recognition according to ISO/IEC 27037 standards
- Erga omnes effectiveness
📊 SOLUTION COMPARISON:
🥇 QUALIFIED TIMESTAMP = Immediate complete solution- ✅ Immediate legal certainty under EU eIDAS
- ✅ Uncontestable SHA-256 hash
- ✅ Maximum evidential value immediately
- ✅ No additional costs later
- ⚠️ First step: strong but not qualified proof
- ✅ Second step: additional cost for authentic copy
- ✅ Final result equivalent to timestamp
- ✅ Uncontestable SHA-256 hash
- ⚠️ Date not legally qualified
- ⚠️ Effective only if no stronger prior evidence is presented
💡 TO PROVE THAT THE FILE IS YOURS:
- 🏆 RECOMMENDED: Qualified timestamp = immediate and complete proof
- 🔄 ALTERNATIVE: Email + later authentic copy
- ⚠️ MINIMUM: Email only (effective if no contestations arise)
- Plagiarism or unauthorized copying
- Disputes between collaborators or former partners
- Copyright, authorship or royalty disputes
- Protection of software patents or algorithms
- Safeguarding creative works under development
❓ Does the system protect me as an OnlyFans or similar platform creator?
Yes, you can certify every content submission even if intended for platforms such as OnlyFans, Fansly, Patreon, or similar. With qualified RFC 3161/eIDAS timestamp you obtain immediate legal protection compliant with EU law.
🏆 MAXIMUM PROTECTION FOR CREATORS: QUALIFIED TIMESTAMP
With the qualified timestamp option, your content gains:- 🏛️ Immediate legal certainty – evidential value under art. 2702 Civil Code
- ⚖️ Opposability erga omnes – contestable only through a false-claim procedure
- 🇪🇺 Recognition throughout the EU without further checks
- 🎯 Complete proof for revenge porn and privacy violations
- 💪 Immediate evidence for legal notices and complaints
Our system generates a certifiable technical page that documents upload date, unique hash, recipient, and file opening (in case of tracked sending). With a qualified timestamp each piece of data acquires immediate legal value. This way, you can definitively prove what you shared, when, and with whom.
If your content is copied, sold, or republished without consent, you can use this evidence to:
- send targeted legal notices and compensation requests already prepared for creators through our ONLINE LEGAL NOTICE service [ click here ];
- request immediate removal from sites or platforms through our ONLINE CONTENT REMOVAL service [ click here ];
- file a complaint for theft, privacy violation, or revenge porn;
- present immediate evidence with EU legal value (if certified with qualified timestamp).
📊 SPECIFIC ADVANTAGES FOR CREATORS:
🥇 WITH QUALIFIED TIMESTAMP:- ✅ Immediate evidence – no waiting time for authentic copy
- ✅ Maximum legal value – effective against revenge porn and violations
- ✅ Lower costs – no additional later expenses
- ✅ International recognition – valid across the EU
- ✅ Evidence for compensation – qualified proof for economic damages
- ⚠️ Authentic copy required – additional cost and time
- ⚠️ Limited evidential value – only a simple presumption
- ⚠️ Longer times – two-step procedure
🛡️ TYPICAL CREATOR CASES:
- Revenge Porn: Proof that the content was private and intended for a specific person
- Content Theft: Demonstrate your temporal priority over illegal copies
- Privacy Violation: Evidence of authorized sending only to specific recipients
- Commercial Plagiarism: Proof for compensation claims and takedown requests
- VIP Client Protection: Tracking of exclusive and customized content
The service is designed to protect creators in a concrete, fast way, with ready-to-use legal tools. With a qualified timestamp your evidence has immediate legal value, ideal for quick action against violations and abuses.
💡 TIP FOR CREATORS: For sensitive or high-value content (custom, exclusive, VIP), always use the qualified timestamp: it guarantees you maximum and immediate legal protection, essential for safeguarding your work and your rights.
❓ Does my file remain private?
Yes, your privacy is 100% guaranteed. With qualified RFC 3161/eIDAS timestamp you also obtain maximum legal security without compromising confidentiality.
🔐 FULL PRIVACY PROTECTION
ContentProtector.eu does not store any files on its own servers. All uploaded content is saved exclusively in a separate personal space on Google Drive owned by ContentProtector.eu, uniquely assigned to each user. Files are stored in restricted folders, accessible only by you and the system, solely for technical purposes related to certification.
🏆 QUALIFIED TIMESTAMP = PRIVACY + LEGAL SECURITY
With qualified timestamp you gain unique privacy advantages:- 🔒 Verification without file access – the SHA-256 hash with eIDAS timestamp is sufficient for legal evidence
- 🏛️ EU Regulation compliance – highest data protection standards
- 🛡️ No inspections needed – the qualified timestamp certifies everything automatically
- ⚡ Immediate evidence – no content access required for later checks
- 🇪🇺 International standards – ISO/IEC 27001 compliance for security
Our system only generates technical data (such as SHA-256 hash, upload date, eIDAS qualified timestamp, and tracking information), maintaining a clear separation between your files and the web platform, in order to guarantee maximum confidentiality and security.
🔐 ACCESS TO CONTENT: ONLY EXCEPTIONAL CASES
Access to content may occur only in two exceptional cases:
- upon explicit request by the user, in case of technical issues or malfunctions;
- upon documented report of unlawful use, abuse, or violation, coming from the recipient or from the competent Authorities.
📊 PRIVACY COMPARISON:
🥇 WITH QUALIFIED TIMESTAMP:- ✅ Maximum privacy – legal checks without file access
- ✅ EU standards – eIDAS Regulation compliance
- ✅ Total autonomy – evidence usable independently
- ✅ Cryptographic security – hash certified by a third-party authority
- ⚠️ Possible verifications – authentic copy may require additional checks
- ⚠️ Service dependency – access may be necessary for some procedures
Even in these rare circumstances, every access is regulated by our Terms and Responsibilities of the Service.
All management is fully automated, with no human intervention, and compliant with the highest standards of security and privacy protection. With qualified RFC 3161/eIDAS timestamp, protection is further strengthened by European cybersecurity standards.
🛡️ ADDITIONAL GUARANTEES FOR SENSITIVE CONTENT:
- OnlyFans/Fansly creators: Maximum protection for intimate and customized content
- Confidential documents: Business security with international standards
- Creative works: Full protection without exposing the content
- Projects in development: Total confidentiality during creative phases
❓ What happens if I find my content copied online?
🔍 WHAT HAPPENS IF I FIND MY CONTENT COPIED ONLINE
Your certification proves WHEN you uploaded the file to our system, creating proof of temporal precedence.⚖️ LEGAL VALUE OF YOUR PROOF
🏆 QUALIFIED TIMESTAMP RFC 3161/eIDAS
RECOMMENDED📧 CERTIFIED EMAIL
🏛️ FORENSIC AUTHENTIC COPY
🎯 WHEN YOUR PROOF HAS MAXIMUM VALUE
| CONTENT TYPE | SCENARIO | STRENGTH OF YOUR PROOF | WHAT THE OTHER PARTY MUST PROVE |
|---|---|---|---|
|
✅ YOUR ORIGINAL CONTENT
Personal videos, private photos, OnlyFans content, creative works, projects, original designs |
No one else has published that content before with demonstrable date | 🔥 MAXIMUM VALUE With qualified timestamp: immediate EU proof Admissible in court without verification | Must prove authorship + prior date certified by qualified authority |
|
⚠️ PRE-EXISTING CONTENT
Material already published online when you uploaded it |
The content was already public before your certification | ⚖️ DEPENDS Whoever has better proof of precedence wins Qualified timestamp still stronger | Must prove publication/creation BEFORE your date with certified evidence |
✅ YOUR ORIGINAL CONTENT
Personal videos, private photos, OnlyFans content, creative works, projects, original designs⚠️ PRE-EXISTING CONTENT
Material already published online when you uploaded it🚀 WHAT YOU CAN DO WITH YOUR CERTIFICATION
- Send formal legal notice through our service [ONLINE LEGAL NOTICES]
- Request removal from websites, social media, search engines
- Support complaints to Cyber Police or competent authorities
- Use in court as immediate qualified evidence
- Claim damages with eIDAS certified proof
💡 WINNING STRATEGY:
🏆 REMEMBER:
With qualified timestamp RFC 3161/eIDAS your proof has immediate maximum legal value! No one can challenge it without allegation of forgery. It’s the strongest protection available.
❓ What happens to my files if I don’t renew my subscription?
The files are automatically deleted from the system, but you can still preserve their legal value by following a few important steps before your plan expires.
Certifications created with ContentProtector remain valid even outside the platform.
Hash + Email → constitute technical evidence documenting the existence of a file on a specific date. However, in case of legal disputes, it is necessary to request the Authentic Forensic Copy (available from the Contacts menu) before the service ends, in order to make it fully admissible as legal evidence.
Hash + Email + Qualified Timestamp (QTSA, eIDAS compliant) → have independent legal value and are fully enforceable across the European Union, even if ContentProtector were no longer online. The qualified timestamp is issued by an accredited Qualified Trust Service Provider (QTSP) and retains its evidential validity regardless of the platform’s status.
📄 Practical note:
It is the user’s responsibility to save a copy of the certification page (for example, using “Print as PDF” from the browser) together with any downloadable files, to ensure proper preservation of evidence.
In summary:
With a qualified timestamp, you are not dependent on our platform.
Without a timestamp, our assistance is required to grant full legal force to your certification — this must be requested before the service ends.
❓ Can I also use ContentProtector for storage?
Yes, every file uploaded to ContentProtector.eu is automatically archived with all elements necessary to ensure its validity over time. With qualified timestamp RFC 3161/eIDAS you get the most secure archiving possible with immediate legal value:
🏆 ARCHIVING WITH QUALIFIED TIMESTAMP – PREMIUM SOLUTION
- 🔐 Certified SHA-256 hash with immediate EU legal value
- 📅 Qualified date certainty compliant with eIDAS Regulation 910/2014
- ⚖️ Qualified probative value – enforceable against third parties
- 🇪🇺 International recognition without additional verification
- 🛡️ Challengeable only with allegation of forgery
📁 STANDARD ARCHIVING ELEMENTS
- SHA-256 Hash (digital fingerprint of the file, unique and immutable)
- Upload date and time via email receipt for each upload (with qualified timestamp: legal date certainty)
- Technical access and tracking data, if the file is sent via link (certified with eIDAS timestamp)
This structure allows the system to be used also as a secure digital archiving tool, particularly useful for:
📂 IDEAL USE CASES FOR CERTIFIED ARCHIVING
- Sensitive or confidential content (creator content, corporate documents, R&D projects)
- Digital evidence to preserve for future legal use (with timestamp: immediate value without authentic copy)
- Projects, contracts, creative drafts, communications or files shared over time
- Creative portfolios with certified temporal protection
- Legal correspondence and important communications
- Forensic backups of valuable content
⚖️ PROBATIVE VALUE OF ARCHIVING
🏆 WITH QUALIFIED TIMESTAMP
- ✅ Immediate legal value – no waiting
- ✅ EU probative archiving – maximum standards
- ✅ Complete autonomy – evidence usable immediately
- ✅ Fixed costs – no extra for legal value
- ✅ Cryptographic security certified by third parties
📧 STANDARD ARCHIVING
- ⚠️ Limited probative value – simple presumption
- ⚠️ Authentic copy required – additional future costs
- ⚠️ Service dependency – subsequent verification
- ✅ SHA-256 hash still strong for integrity
All data is verifiable and preserved in unalterable form. With qualified timestamp you have immediate legal value; otherwise you can obtain at any time a forensic authentic copy to support any legal needs.
Unlike simple cloud storage, this archiving has technical and probative value, because it’s linked to a documentary structure that is traceable, certifiable and demonstrable. With qualified timestamp RFC 3161/eIDAS, you get the highest standard of legal archiving available.
⚠️ IMPORTANT: SERVICE RENEWAL
Just remember to renew the service periodically:
if the subscription expires, all data connected to your account (including certified files, hashes and tracking) will be permanently deleted also for security and privacy reasons.
